Info
I haven’t finished writing this blog post, but I published it so the already-written information can be read by you. I will improve this post one day™.
PGP, gpg, GnuPG, OpenPGP… what is it?
TL;DR
- PGP (Pretty Good Privacy) is the original proprietary software package
- OpenPGP is the open standard defined by RFC4880
- GnuPG (GNU Privacy Guard), often abbreviated as GPG, is a complete and free implementation of the OpenPGP standard
gpgis the command used on Unix systems to work with GnuPG
The GNU Privacy Guard · gnupg.org
GnuPG is a complete and free implementation of the OpenPGP standard as defined by RFC4880 (also known as PGP). GnuPG allows you to encrypt and sign your data and communications; it features a versatile key management system, along with access modules for all kinds of public key directories. GnuPG, also known as GPG, is a command line tool with features for easy integration with other applications. A wealth of frontend applications and libraries are available. GnuPG also provides support for S/MIME and Secure Shell (ssh).
Since its introduction in 1997, GnuPG is Free Software (meaning that it respects your freedom). It can be freely used, modified and distributed under the terms of the GNU General Public License.
RFC4880 “OpenPGP Message Format”, mentioned by GnuPG, was only published in November 2007 but it obsoletes older RFC2440 “OpenPGP Message Format” (November 1998) and RFC1991 “PGP Message Exchange Formats”(August 1996). PGP is a long-living standard.
GPT-3.5, 2023-12-10 (with some formatting improvements)
GPG (GNU Privacy Guard) and PGP (Pretty Good Privacy) are both cryptographic software used for encryption, decryption, digital signatures, and securing communication. They provide similar functionalities and share common goals of ensuring data confidentiality and integrity, but they have different origins and implementations.
PGP (Pretty Good Privacy)
- Origin: PGP was developed by Phil Zimmermann in the early 1990s. It was initially released as a proprietary software package for encrypting and securing email communications.
- Features: PGP offers various cryptographic functionalities such as encryption, decryption, digital signatures, and secure email communication. It gained popularity for its strong encryption capabilities and was widely used for securing emails and files.
- Ownership: PGP was initially a proprietary software owned by various companies over the years. Symantec Corporation acquired PGP Corporation, which further developed and maintained the PGP software suite.
GPG (GNU Privacy Guard)
- Origin: GPG, on the other hand, is an open-source implementation of the OpenPGP standard. It was developed by Werner Koch and released as free software as part of the GNU Project.
- Compatibility: GPG aims to be compatible with the OpenPGP standard defined in RFC 4880. It implements the OpenPGP protocol for secure communication and encryption.
- Open Source: GPG is distributed under the GNU General Public License (GPL) and is free to use, modify, and distribute. Being open-source, GPG is transparent and subject to community-driven development and scrutiny.
Differences
- Licensing and Ownership: PGP started as a proprietary software with various ownerships over time, while GPG is an open-source implementation distributed under a free software license.
- Development Model: GPG’s development is open and community-driven, while PGP’s development was initially proprietary and later continued under commercial entities.
- Compatibility: Both GPG and PGP adhere to the OpenPGP standard, which means they are designed to be interoperable with each other and other software that follows the same standard.
In summary, while GPG and PGP serve similar purposes and follow the same OpenPGP standard, the key differences lie in their origins, licensing, development models, and ownership history. GPG is a free and open-source implementation of the OpenPGP standard, while PGP was initially a proprietary software later maintained by commercial entities.
Some GPG-related cryptography vocabulary
Tip
If you’re familiar with cryptography, you can jump to the next section.
Asymmetric cryptography
Public-key cryptography · Wikipedia
Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Key pairs are generated with cryptographic algorithms based on mathematical problems termed one-way functions. Security of public-key cryptography depends on keeping the private key secret; the public key can be openly distributed without compromising security.
In a public-key encryption system, anyone with a public key can encrypt a message, yielding a ciphertext, but only those who know the corresponding private key can decrypt the ciphertext to obtain the original message.
What’s inside a GPG key?
A GPG key is not just a single key, as it consists of four parts:
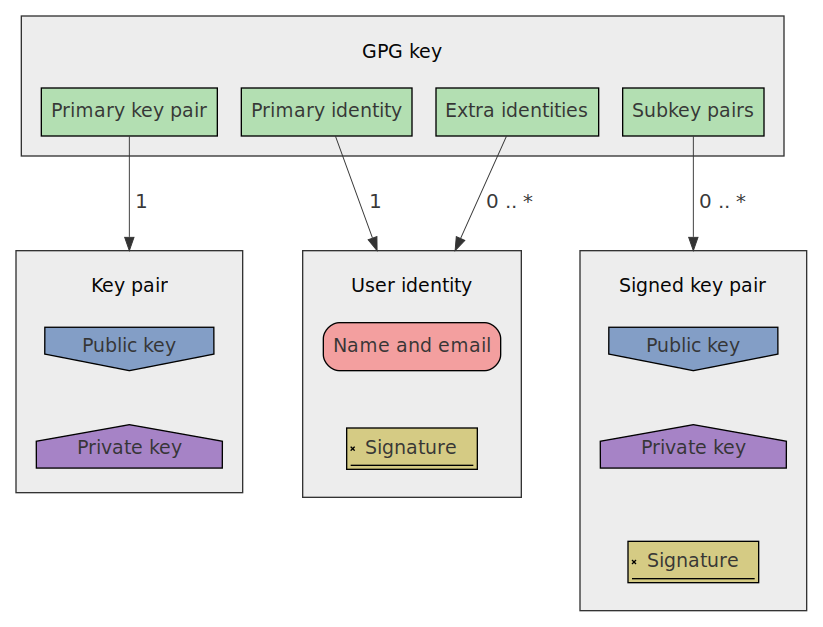
This image, coming from “Setting up GnuPG + Yubikey on NixOS for SSH authentication”, explains quite well what a GPG key contains, but let’s get a bit more in-depth:
-
Primary key pair
The primary key pair, also called “master key”, is the root key used to create other key pairs, called subkey pairs.
-
Primary identity
The primary identity, also called “user identity” or “uid”, contains information about the owner of the key (name and email).
Info
From what I know, identities are not verified as keys are generated offline. However, some key servers might perform additional checks to ensure a key is published by the entity described by the primary identity.
-
Extra identities
A GPG key can contain extra identities linked to the primary key pair. It can be used to define multiple email addresses for example.
Info
From what I know, identities are not verified as keys are generated offline. However, some key servers might perform additional checks to ensure a key is published by the entity described by the primary identity.
-
Subkey pairs
Setting up GnuPG + Yubikey on NixOS for SSH authentication
Subkey pairs are basically normal key pairs that have a signature that associates them to the primary key pair. When a subkey pair is created, the primary private key is used to create this signature. The reason why you would want to create subkey pairs is because in GPG you can specify what actions a key pair is allowed to perform.
Some GPG concepts
Capabilities
There are 4 different actions a key pair can perform: Certify, Sign, Encrypt and Authenticate:
-
Certify (
C)Setting up GnuPG + Yubikey on NixOS for SSH authentication
The most powerful action is called Certify (
C), which allows a key pair to create subkey pairs from itself. A subkey pair is just a key pair but with a signature that associates it to another key pair. The primary key pair will therefore always have the Certify capability, so that it can create subkey pairs. -
Sign (
S)Signing files, emails, etc.
-
Encrypt (
E)Encrypting files, emails, etc.
-
Authenticate (
A)Authenticating against external services, such as SSH
GPG key ID
TODO: https://unix.stackexchange.com/a/613909
Expiry
TODO
Refresh
TODO